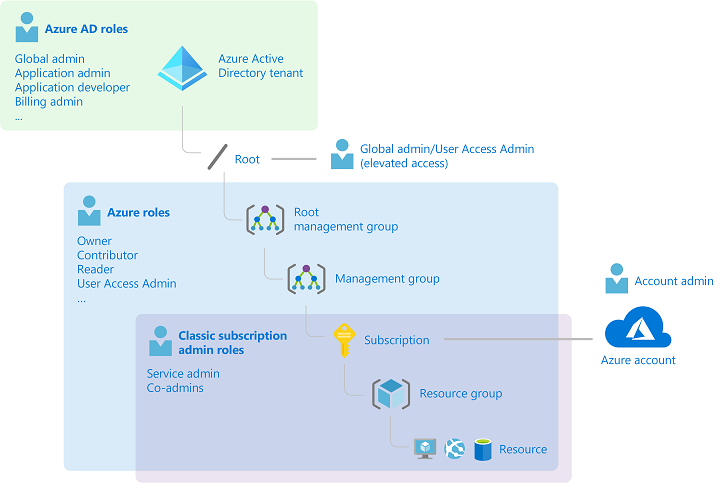
reference – https://learn.microsoft.com/en-us/azure/role-based-access-control/rbac-and-directory-admin-roles
https://learn.microsoft.com/en-us/azure/role-based-access-control/overview
Here is a comparison chart of common Azure built-in roles and their access to resources.
| Role Name | Description | Access to Resources | No Access to Resources |
|---|---|---|---|
| Owner | Has full access to all resources and can manage access to resources. | Can create, read, update, and delete all resources within the subscription. Can also grant permissions to others. | The Service Administrator and Co-Administrators are assigned the Owner role at the subscription scope Applies to all resource types. |
| Global Administrator | Provides full access to all Azure services and resources. | Can manage all aspects of Azure, including subscription management, resource management, and identity and access management. | N/A |
| Contributor | Can create and manage all types of resources, but can’t grant access to others. | Can create, read, update, and delete all resources within the subscription, except for access control. | Access control operations, such as granting or revoking access to resources. |
| Reader | Can view existing resources. | Can view all resources within the subscription, but can’t make any changes. | Write or modify operations, such as creating or deleting resources. |
| User Access Administrator | Can manage user access to resources. | Can manage access to resources within the subscription, but can’t create or modify resources. | Resource management operations, such as creating or deleting resources. |
| Security Administrator | Can manage security-related operations. | Can manage security-related operations, such as creating and managing security policies, but can’t create or modify resources. | Resource management operations, such as creating or deleting resources. |
| Network Contributor | Can create and manage virtual networks and associated resources. | Can create, read, update, and delete virtual networks, subnets, network interfaces, and network security groups. | Resource management operations, such as creating or deleting resources, outside of virtual networks. |
| Storage Account Contributor | Can create and manage storage accounts and associated resources. | Can create, read, update, and delete storage accounts, containers, and blobs. | Resource management operations, such as creating or deleting resources, outside of storage accounts. |
| SQL Server Contributor | Can create and manage SQL servers and databases. | Can create, read, update, and delete SQL servers and databases. | Resource management operations, such as creating or deleting resources, outside of SQL servers and databases. |
| App Service Contributor | Can create and manage App Service plans and associated resources. | Can create, read, update, and delete App Service plans, web apps, and deployment slots. | Resource management operations, such as creating or deleting resources, outside of App Service plans and associated resources. |
| Monitoring Contributor | Can manage monitoring-related operations. | Can manage monitoring-related operations, such as creating and managing monitoring policies, but can’t create or modify resources. | Resource management operations, such as creating or deleting resources, outside of monitoring-related operations. |
Note that this is not an exhaustive list of all Azure built-in roles and their access to resources, and that the specific permissions associated with each role may vary depending on the specific Azure resources being managed. For more details about built in roles please refer below link.
Built-In roles link- https://learn.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
Here is a comparison chart highlighting some of the key differences between the Owner ,Global Administrator and User Administrator roles in Azure:
| Role | Purpose | Permissions | Scope |
|---|---|---|---|
| Owner | Has full access to all resources in the subscription, and can delegate access to others | Can create, read, update, and delete all resources and resource groups in the subscription | Applies to a single subscription (Subscription Wise) |
| Global Administrator | Has full access to all Azure services and resources, and can delegate access to others | Can manage access, settings, and configurations for all Azure services and resources, including subscriptions, resource groups, and individual resources | Applies to all subscriptions and Azure AD resources (Tenant Wise) |
| User Administrator | Can manage user accounts and reset passwords | Can create, read, update, and delete user accounts and reset passwords; can manage user groups and their memberships; can assign roles to users and can manage some Azure resources such as virtual machines and storage accounts. | Can manage access to all resources and can create and manage some Azure resources within specific resource groups.(Resource-specific) |
| Billing Administrator | Can manage billing information, including managing subscriptions and changing billing details. | Can manage billing information, including the ability to change billing details and manage subscriptions. | Has access to all billing information and can manage subscriptions associated with the billing account. |
While both the Owner and Global Administrator roles have full access to resources in Azure, there are some key differences between the two roles. The Owner role is specific to a single subscription, while the Global Administrator role applies to all subscriptions and Azure AD resources. The Global Administrator role also includes permissions for managing access, settings, and configurations for all Azure services and resources, while the Owner role is limited to managing resources within a single subscription.
In general, it is recommended to grant the Global Administrator role only to users who require broad access to Azure resources across multiple subscriptions, while the Owner role can be used to grant full access to resources within a single subscription.
User Administrator has more limited permissions compared to Owner and Global Administrator, but is focused specifically on managing user accounts and groups within Azure.
It is important to carefully manage access to resources within your Azure subscriptions to ensure that only authorised users and applications have access to sensitive data and configurations. You should assign roles with the minimum permissions necessary to perform the required tasks.
Here is a comparison chart of common Azure built-in roles and their permissions for different operations (Create/Rename/Move/Delete/Assign Access/Assign Policy/Read Operations) on management groups:
| Role Name | Create | Rename | Move | Delete | Assign Access | Assign Policy | Read Operations |
|---|---|---|---|---|---|---|---|
| Owner | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Global Administrator | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Contributor | ✔ | ✔ | ✔ | ✔ | ✘ | ✘ | ✔ |
| Management Group Contributor | ✔ | ✔ | ✔ | ✔ | ✘ | ✘ | ✔ |
| Reader | ✘ | ✘ | ✘ | ✘ | ✘ | ✘ | ✔ |
| Management Group Reader | ✘ | ✘ | ✘ | ✘ | ✘ | ✘ | ✔ |
| User Access Administrator | ✘ | ✘ | ✘ | ✘ | ✔ | ✔ | ✘ |
| Resource Policy Contributor | ✘ | ✘ | ✘ | ✘ | ✘ | ✔ | ✘ |
| Security Administrator | ✘ | ✘ | ✘ | ✘ | ✘ | ✘ | ✘ |
| Network Contributor | ✘ | ✘ | ✘ | ✘ | ✘ | ✘ | ✘ |
Add users and Assign Permission –https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/add-users-azure-active-directory?view=azure-devops
